Introduction:
In the world of information security, risk management is of utmost importance. Risk management is the process of identifying, assessing, and mitigating risks with the aim to safeguard critical and sensitive data and maintain its confidentiality, integrity, and availability. Organizations should conduct risk assessments on a regular basis with the goal of moving towards a more systematic and comprehensive approach to risk management that yields valid, consistent, and comparable results when repeated. This four-part series explores the risk management lifecycle, beginning with the fundamental concepts covered in this first part.
1). Establishing the context:
Before we begin addressing the risks, we must understand the context of the organization. This involves the following,
-
- Identify key stakeholders, such as customers, employees, regulatory agencies, and suppliers, who have an interest in the organization’s information security.
- Outline the objectives and information security-related policies of the company.
- Establish the parameters of the risk management process, including the locations, procedures, and assets that are covered.
- Understand the legal, regulatory, and contractual requirements pertaining to information security.
Example of establishing context:
A financial organization aims to establish an ISMS that is aligned with ISO 27001. In this context, their objectives include ensuring the confidentiality of customer financial data and complying with financial regulations. They have identified key stakeholders such as customers, the central bank, and regulatory authorities. The scope of their risk management efforts includes all customer data and financial operations.
2). Define the risk criteria:
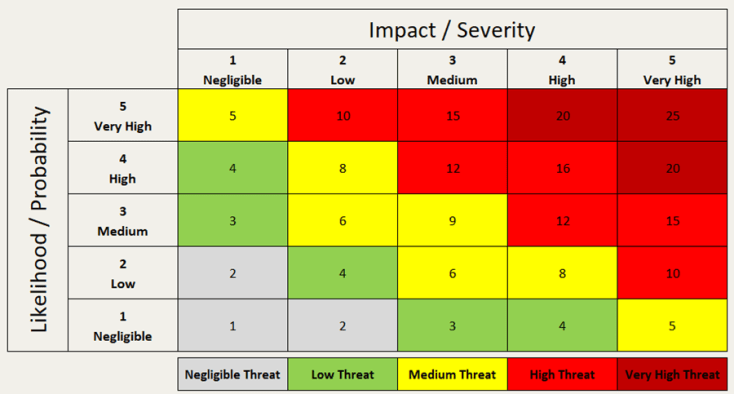
Risk criteria are the benchmarks for evaluating and measuring risks with the aim of determining whether they need to be mitigated, accepted, avoided, or transferred. In general, risk criteria should comprise a risk scoring system that includes risk factors, predetermined risk level scales, and a risk matrix for an organization to quantify risk to prioritize and make informed decisions. As part of the entire risk assessment process, many of the risk assessment criteria are related to defining the scoring or rating of risk, including the likelihood and impact of the risk.
Example or risk criteria:
3). Risk Assessment:
Risk assessment is a fundamental component of information security. It entails identifying, analyzing, and evaluating risks to an organization’s information assets. This phase involves:
-
- Identifying assets: Determine what information assets are critical to your organization.
- Identifying threats: Recognize potential risks, such as data breaches, natural disasters, or human errors and determining the likelihood and impact.
- Assessing vulnerabilities: Examine weaknesses in your security controls that could be exploited.
- Calculating risk: Evaluate the likelihood and impact of each risk to determine its significance.
Examples:
-
- People: A lack of employee security awareness and adherence can lead to sensitive data exfiltration.
- Process: Absence of patch management policy may expose system vulnerabilities over time.
- Technology: Outdated and unsupported software / hardware is susceptible to security vulnerabilities and exploits.
- Physical: Inadequate physical access control will allow unauthorized individuals to enter sensitive premises without permission.
4). Risk Treatment:
After identifying, analyzing and evaluating risks, we must decide how to manage them. This includes selecting risk treatment strategies, which may involve risk mitigation, risk acceptance, risk avoidance, or risk transfer. We will then establish a risk treatment plan to implement the chosen strategies.
5). Risk Monitoring and Review:
Risk management is an ongoing process. Regularly monitoring and reviewing the risk management activities ensures that the organization remains secure and compliant. This phase involves:
- Monitoring changes: Staying vigilant about any alterations in the information security landscape.
- Updating the risk treatment plan: As circumstances change, adjust the strategies accordingly.
- Continuously improving: Learning from past experiences and refining the risk management process.
Conclusion:
By establishing this solid foundation, we can pave the way for an effective risk management lifecycle. In the following parts of this series, we will delve deeper into each phase, providing practical examples and a more detailed guide to risk assessment, risk treatment, and risk monitoring and review.
