In Part 1 and Part 2 of our series, we explored the fundamentals of the risk management lifecycle and the detailed process of risk assessment. Now, we delve into the critical phase of Risk Treatment. This phase involves selecting and implementing measures to mitigate, transfer, avoid, or accept identified risks.
1. Selecting Risk Treatment Options:
Once risks have been identified and assessed, organizations must decide how to address them. Many standards offer four primary risk treatment options:
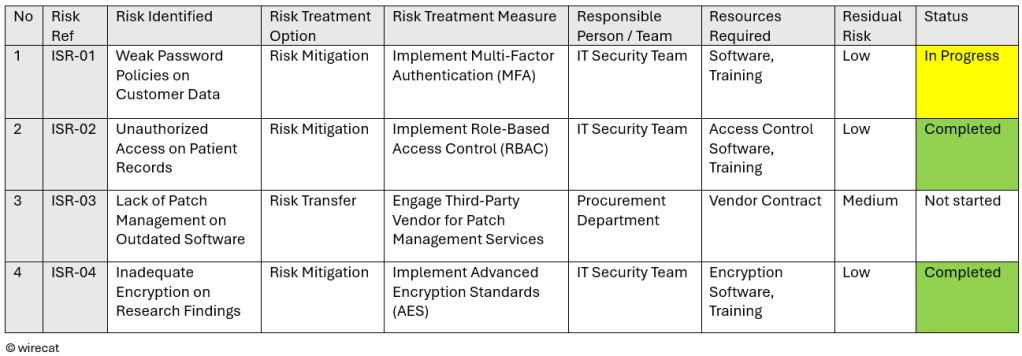
– Risk Mitigation: This option involves implementing measures to reduce the likelihood or impact of identified risks to an acceptable level. Organizations choose this option when they want to proactively address risks while allowing the business to continue its operations. For example, implementing Multi-Factor Authentication (MFA) helps mitigate the risk of unauthorized access by adding an additional layer of security beyond passwords.
– Risk Transfer: Organizations opt for risk transfer when they want to shift the responsibility for managing the risk to a third party. This option is chosen when the organization lacks the resources or expertise to manage the risk internally. Engaging a third-party vendor for Patch Management Services allows the organization to transfer the risk of managing software vulnerabilities to a specialized provider.
– Risk Acceptance: Organizations choose risk acceptance when they recognize a risk but deliberately decide not to take any further action. This option is typically chosen for risks with low likelihood or impact that fall within acceptable tolerance levels. For example, the organization may accept the risk of weak password policies for less critical systems where the potential impact of a security breach is negligible/minimal.
– Risk Avoidance: Risk avoidance involves eliminating the risk altogether by ceasing the activity or process that poses the risk. While effective, this option may not always be feasible or practical. Organizations may choose risk avoidance when the potential impact of the risk is severe, and there are viable alternatives available. However, it may also result in missed opportunities or increased costs. For example, the organization may decide to avoid the risk of unauthorized access to sensitive data by discontinuing remote access for certain employees.
2. Developing a Risk Treatment Plan:
Once risk treatment options have been selected, organizations must develop a comprehensive risk treatment plan. This plan outlines the specific actions, responsibilities, timelines, and resources required to implement the chosen risk treatment measures.
Example:
For a financial institution, if the risk assessment identifies a high-risk of unauthorized access to financial records due to weak password policies, the risk treatment plan may include:
– Implementing multi-factor authentication (MFA) for accessing financial systems.
– Conducting regular password security training for employees.
– Enforcing password complexity requirements.
3. Implementing Risk Treatment Measures:
With the risk treatment plan in place, organizations proceed to implement the identified risk treatment measures. This may involve deploying new technologies, updating policies and procedures, providing training to employees, or engaging third-party vendors.
Conclusion:
In Part 3 of our series on the risk management lifecycle, we explored the critical phase of Risk Treatment. This phase involves selecting and implementing measures to mitigate, transfer, avoid, or accept identified risks.
Key Points:
– Risk Mitigation: Organizations proactively address risks by implementing measures to reduce their likelihood or impact. This option allows businesses to continue operations while enhancing security controls and safeguards.
– Risk Transfer: Shifting the responsibility for managing risks to a third party can be an effective strategy when organizations lack the resources or expertise to manage risks internally. Engaging third-party vendors or purchasing insurance are common risk transfer methods.
– Risk Acceptance: Recognizing a risk but consciously deciding not to take further action is a valid approach for risks with low likelihood or impact that fall within acceptable tolerance levels. Risk acceptance allows organizations to focus resources on higher-priority risks.
– Risk Avoidance: Eliminating risks altogether by ceasing activities or processes that pose risks is an effective but often impractical strategy. Organizations may choose risk avoidance when the potential impact of the risk is severe and viable alternatives are available.
Considerations for Decision-making:
– Cost: Evaluation of the costs associated with each risk treatment option, including implementation, maintenance, and potential impact on the organization’s budget.
– Effectiveness: Assessment of how effectively each option addresses identified risks and reduces the organization’s overall risk exposure.
– Feasibility: Consideration of the organization’s capabilities and resources to implement and sustain each risk treatment measure.
By carefully considering these factors and evaluating the potential benefits and drawbacks of each risk treatment option, organizations can make informed decisions to effectively manage and mitigate risks to their information assets.
In Part 4 of our series, we will explore the final phase of the risk management lifecycle: Risk Monitoring and Review. Stay tuned for practical insights and guidance on maintaining the effectiveness of your risk management efforts.
