Introduction
In the bustling realm of cybersecurity, where threats advance as quickly as technology itself, organizations must navigate a risky landscape filled with potential vulnerabilities. To effectively manage these risks, it’s essential to employ a structured framework that incorporates Key Risk Indicators (KRIs) and Key Performance Indicators (KPIs). Let’s dive you into my personal experience that highlights the significance of these metrics in a real-world context.
The Journey Begins: Understanding KRIs and KPIs
As a security professional in a medium-sized organization, I was tasked with leading a project to enhance our security posture after experiencing a security breach. Our goal was not only to protect our assets but also to ensure the resilience of our systems amidst the ever-present threats of cyberattacks. Our first step was to identify our KRIs.
Stage 1: Identifying Key Risk Indicators (KRIs)
Identifying KRIs is akin to setting a compass in uncharted waters. KRIs are the metrics that signal potential risks to an organization’s security posture. By identifying these risks early, organizations can focus on prevention and mitigation strategies.
Key Aspects for Designing KRIs
To craft effective KRIs, we focused on several key aspects:
– KRI should be linked to a specific risk: Each KRI we defined was closely tied to known vulnerabilities in our systems, ensuring relevance and focus.
– KRI should be capable of predicting a risk event: Our indicators needed to serve as early warning systems, allowing us to foresee potential incidents before they escalated.
– KRI should be complete and accurate: We ensured the information derived from our KRIs was comprehensive and precise, forming a solid foundation for our risk management decisions.
– KRI should be easily measurable and comparable: The indicators had to be quantifiable, enabling us to track changes and assess the effectiveness of our strategies over time.
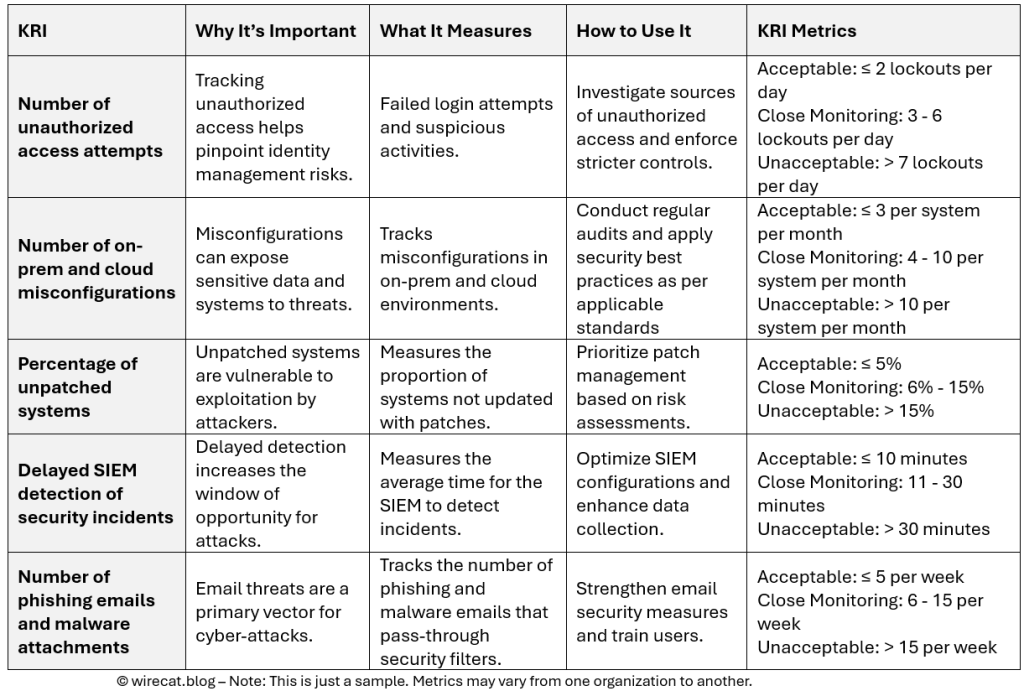
As we defined our KRIs, we also needed to ensure they were effectively monitored and managed to ensure they align with the organization’s evolving security landscape. One thing to note here is that KRIs are operational in nature.
Stage 2: Establishing Key Performance Indicators (KPIs)
Once our KRIs were in place, it was time to establish KPIs that would help us measure the effectiveness of our risk management efforts. KPIs measure how well security controls and response mechanisms are functioning.
Key Aspects for Designing KPIs
We paid careful attention to the following aspects while designing our KPIs:
– KPI should be SMART: Our KPIs were crafted to be Specific, Measurable, Achievable, Reliable, and Timely, ensuring they provided valuable insights.
– KPI should provide value to the business: Each KPI was aligned with our organizational goals, guaranteeing its relevance.
– KPI should be linked to specific business goals: KPIs needed to connect directly to our strategic objectives to drive meaningful results.
– KPI should be measurable and comparable over a period of time: Our KPIs allowed us to track performance trends, informing our future decisions.
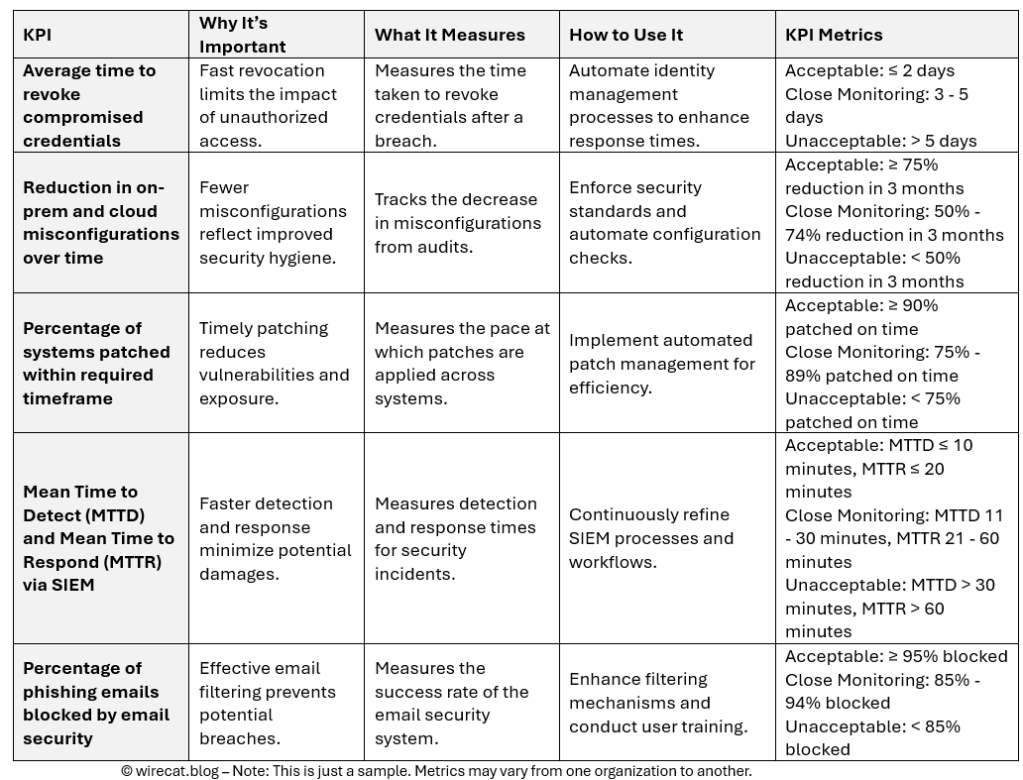
Monitoring these KPIs helps organizations maintain a balance between strong security measures and operational efficiency, while continuously improving security strategies. One thing to note here is that KPIs are strategic in nature.
Stage 3: Monitoring and Adapting the Framework
Having identified our KRIs and KPIs, the next step was to ensure their effectiveness through regular monitoring and adaptations. We set up a dashboard that displayed real-time data on each indicator, allowing us to make informed decisions on the fly.
Importance of Regular Review
We scheduled monthly reviews to assess the trends reflected in our KRIs and KPIs. If we noticed any concerning patterns, such as a rising number of unauthorized access attempts or a spike in phishing emails, we quickly adjusted our strategies, implemented additional training for staff, or enhanced our technical controls.
Feedback Loops
Engaging with team members across departments helped us gather valuable feedback on the effectiveness of our measures. Their insights often revealed gaps we hadn’t anticipated, leading to continuous improvement in our security posture. For instance, the customer support team reported an increase in suspicious emails bypassing our email security filters. Their insights allowed us to identify patterns of phishing attempts evading detection. We collaborated with our email security vendors to refine filtering systems and updated user training, which led to a significant increase in our phishing block rate
Stage 4: Implementation and Continuous Improvement
With our KRIs and KPIs established and monitored, it was time for the critical stage of implementation. This phase involved translating our strategies into actionable steps across the organization.
Creating an Implementation Plan
We developed a comprehensive implementation plan that outlined roles, responsibilities, timelines, and resource allocations. This plan ensured that every team member understood their part in enhancing our security posture.
Training and Awareness Programs
Recognizing that technology alone cannot safeguard us, we initiated regular training sessions to educate employees about security best practices. Topics included recognizing phishing emails, securing credentials, and understanding the importance of reporting suspicious activities.
Regular Assessments and Refinements
Implementation was not a one-time event, it required ongoing assessments. We established a schedule for internal audits to evaluate the effectiveness of our KRIs and KPIs. If certain indicators were not yielding the desired outcomes, we revisited and refined them to better suit our evolving landscape.
Emphasizing Continuous Improvement
We embraced a culture of continuous improvement, where lessons learned from incidents and near-misses were analysed to enhance our security strategies. Regular workshops and brainstorming sessions with the security team and stakeholders kept the focus on innovation and adaptation in our approach.
Leveraging Technology
Utilizing advanced security tools and solutions also played a crucial role in our implementation efforts. We integrated automation into our monitoring processes, ensuring that our KRIs and KPIs were not only measurable but also actionable in real time.
Conclusion
Managing security risk through KRIs and KPIs is not merely a box-ticking exercise but a dynamic, evolving process. By following the stages of identifying KRIs, establishing KPIs, monitoring their effectiveness, and implementing continuous improvement measures, organizations can significantly enhance their security posture. In the ever-changing landscape of cybersecurity, a proactive and adaptive approach is the key to success.
As we embark on our journey of security risk management, remember that the cybersecurity landscape is ever evolving. Engage with your teams, continuously refine your processes, and always keep a keen eye on emerging threats. Your organization’s security resilience depends on it.

Leave a comment