In the previous post, we saw how compliance brings structure, accountability, and trust to cybersecurity. It sets the stage for order in a chaotic landscape.
But here’s where the story turns — and where many organizations stumble.
After the certificates are framed and the audit reports are filed, there’s often a quiet assumption that “we’re safe now.” The board relaxes, budgets tighten, and attention shifts elsewhere. Yet attackers don’t pause because your audit just ended.
The uncomfortable truth is this: compliance does not always mean security.
The Illusion of Safety
Compliance is often mistaken for immunity — a belief that once all boxes are ticked, the organization is protected. But the real world operates differently. Cyber threats evolve faster than any standard can be updated, and attackers don’t read your audit report before they strike.
Think of compliance as a snapshot — a photograph of your security posture on the day of the audit. Security, on the other hand, is a real-time video feed. It changes by the hour, influenced by new vulnerabilities, insider behaviors, and evolving adversary tactics.
This gap between being compliant and being secure is where most breaches happen.
Why Compliance Falls Short
- Point-in-Time vs. Continuous Threats
Compliance validates that controls exist; it doesn’t ensure they remain effective. You might pass an ISO 27001 audit in February and get breached in March because a misconfigured cloud bucket went unnoticed. - Checklists ≠ Context
Many frameworks focus on the presence of controls, not the quality or relevance of those controls. A firewall rule might meet compliance criteria, yet still allow lateral movement if misconfigured. - Minimum Standards, Not Maximum Defense
Most compliance frameworks define minimum acceptable practices. Threat actors, however, operate at maximum creativity. They exploit the gaps between compliance and reality. - Uniform Frameworks, Unique Threats
Compliance frameworks apply broadly — a retail chain and a mining operation might both follow the same ISO 27001 clauses. But their risk landscapes, exposure, and attack vectors differ dramatically. Without contextual adaptation, compliance can become misaligned with actual risk.
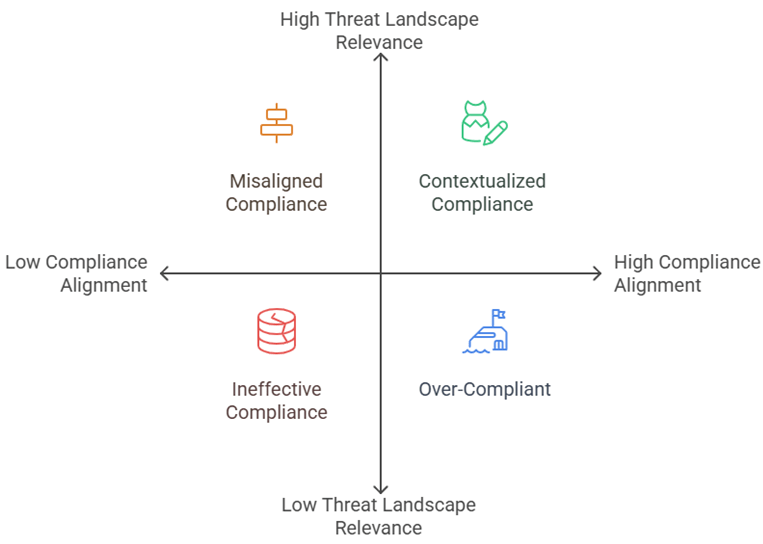
Fig 2.1: Compliance vs Threat Landscape Alignment
Real-World Lessons: When Compliance Wasn’t Enough
Target (2013)
Target was PCI-DSS compliant before attackers compromised a third-party vendor, infiltrated the network through HVAC systems, and stole 40 million payment card records. Controls were present on paper but not continuously enforced in practice. The result was one of the costliest breaches in retail history.
Equifax (2017)
Despite maintaining compliance certifications, Equifax failed to patch a known vulnerability in Apache Struts. The oversight led to the exposure of personal data for 147 million individuals. Compliance didn’t fail — operational follow-through did.
Optus and Medibank (Australia, 2022)
Both organizations operated under Australia’s stringent Privacy Act and industry compliance requirements. Yet, massive breaches still occurred. The Optus data breach exposed sensitive information of 10 million Australians, and Medibank’s attack compromised 9.7 million health records. These incidents underscored a painful truth: compliance frameworks cannot compensate for misconfigurations, third-party risks, and delayed detection capabilities.
Colonial Pipeline (2021)
Regulatory compliance didn’t prevent a ransomware attack that halted fuel delivery across the U.S. East Coast. Weak password hygiene on a single VPN account led to an operational shutdown that cost millions. The system was compliant — just not secure.
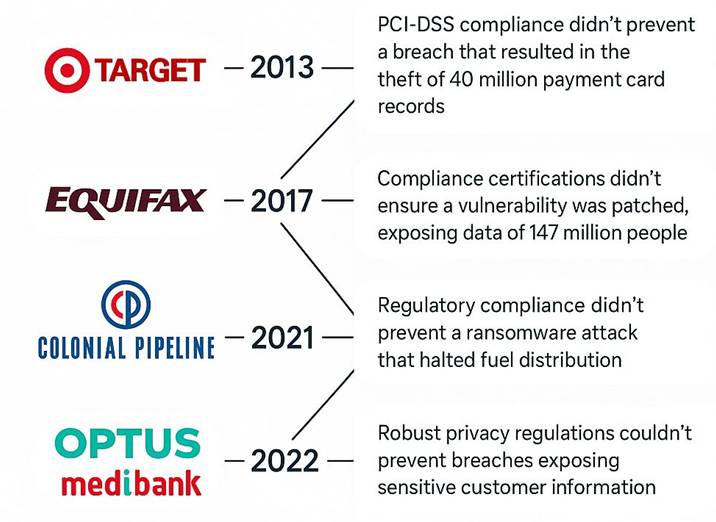
Fig 2.2: When Compliance Wasn’t Enough
The Dangerous Comfort Zone
Compliance often creates what experts call the “illusion of control.”
Organizations invest heavily to pass audits, document evidence, and satisfy regulators — but not necessarily to test how those controls perform under pressure.
In many cases, controls exist without validation:
- Incident response plans that are never tested.
- Backups that are never restored.
- SIEM alerts that no one reviews.
When real attacks occur, those “compliant” controls crumble. The result? A breach that surprises leadership — even though every box was ticked.
Conclusion – Compliance Is the Report Card, Not the Reality
Compliance is essential, but it’s not the same as resilience. It provides the language for accountability but not the muscle for defense. It can tell you what you have, but not whether it actually works.
An organization can be fully compliant and still be one unpatched server, one misconfigured firewall, or one insider click away from compromise.
Compliance is the report card — security is the exam you must pass every day.
In the next post, we’ll explore how mature organizations bridge this gap — turning compliance from a static requirement into a dynamic, risk-driven security strategy that truly protects.
