In our journey so far, we’ve seen how compliance brings order to cybersecurity (Part 1), and how over-reliance on it can create blind spots (Part 2).
Now, we turn to the most critical part of the story — how organizations bridge that gap and turn compliance into real, measurable security resilience.
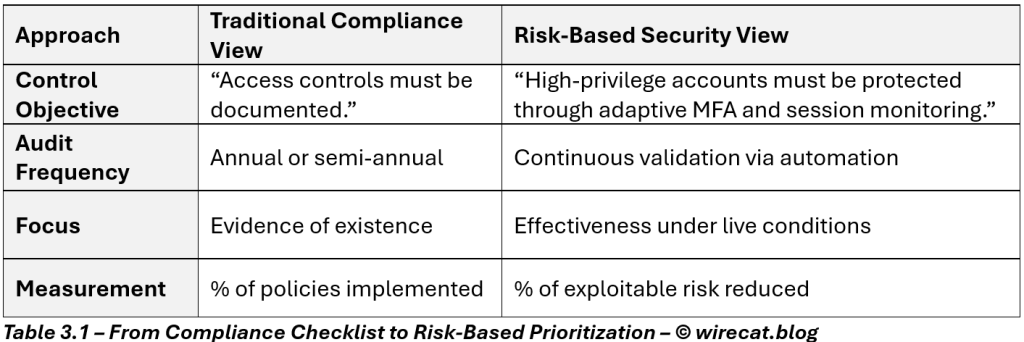
Compliance sets the minimum standard; security transforms it into a living system that defends, detects, and adapts.
1️⃣ Adopting a Risk-Based Mindset
Compliance tells you what to do; risk-based security tells you why it matters.
Instead of managing controls equally, mature organizations prioritize them by threat likelihood, business impact, and exposure.
For example, mapping controls to MITRE ATT&CK techniques and assigning risk scores provides clarity on where to invest.
2️⃣ From Annual Audits to Continuous Assurance
Cyber risk doesn’t operate on an audit schedule.
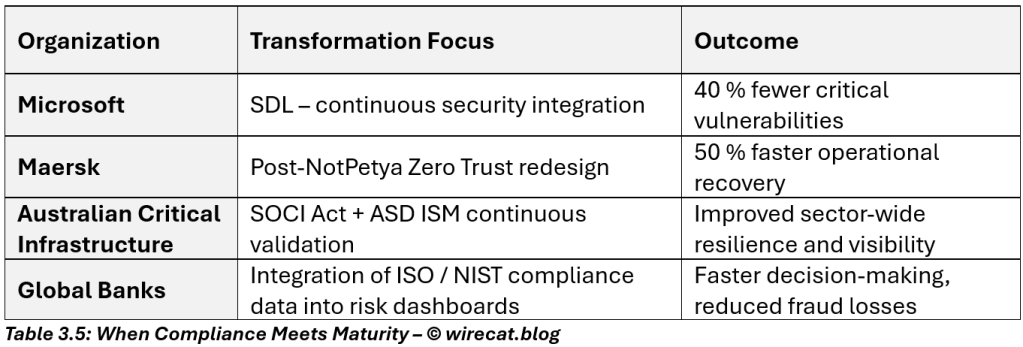
Leading organizations move toward continuous compliance and monitoring, combining frameworks such as NIST CSF, ASD ISM, and ISO 27001 with real-time detection tools like XDR, SIEM, and SOAR.
🧭 Example: Microsoft’s Security Development Lifecycle (SDL)
After facing security challenges in the early 2000s, Microsoft integrated SDL — embedding security checks, code analysis, and threat modeling into every release cycle.
Result: A 40 % reduction in critical vulnerabilities year-over-year and a security-by-design culture still in place today.
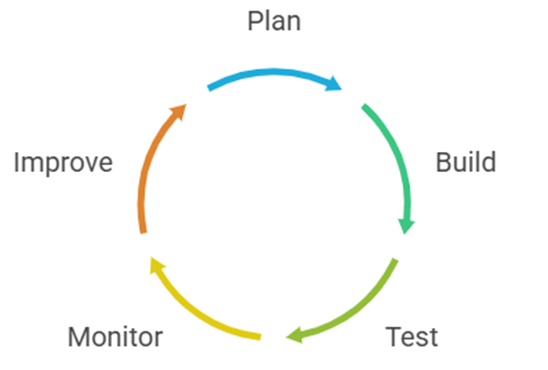
Fig 3.1: Microsoft Security Development Lifecycle
3️⃣ Testing Controls Under Real-World Conditions
Policies don’t stop attacks — practice does.
Organizations that bridge compliance and security test their defenses with red teaming, purple teaming, and adversary simulations to verify whether controls actually work.
🛡 Case Study: Maersk, Post-NotPetya (2017)
Maersk was globally compliant before the NotPetya ransomware attack crippled its operations. Afterward, it rebuilt with Zero Trust segmentation, rapid recovery mechanisms, and continuous security validation.
Outcome: a 50 % faster recovery capability and recognition as a benchmark in cyber resilience.

4️⃣ Integrating Compliance into Governance and Decision-Making
Instead of treating compliance and security as separate lanes, mature enterprises fuse them into a single governance ecosystem.
Compliance evidence becomes data for decision-making — feeding risk dashboards, board reports, and security KPIs.
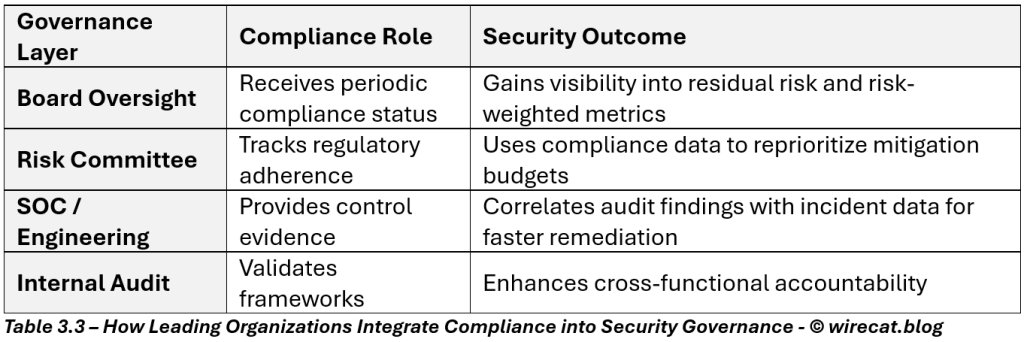
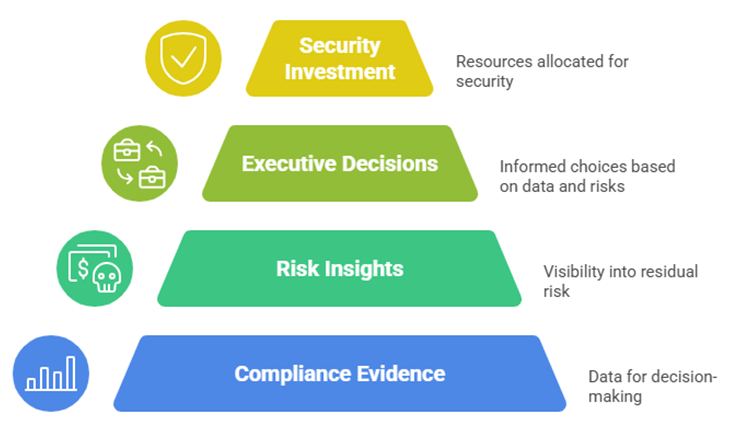
Fig 3.2: Compliance Integration Pyramid
5️⃣ Building a Security-First Culture
Compliance defines the rules; culture determines whether they’re followed.
Organizations that cultivate a security-first mindset invest in continuous education, reward proactive reporting, and link security objectives to performance metrics.
Example: Australian government agencies applying the ASD Essential Eight maturity model run scenario-based workshops simulating phishing, privilege misuse, and ransomware events — reinforcing awareness through realism.
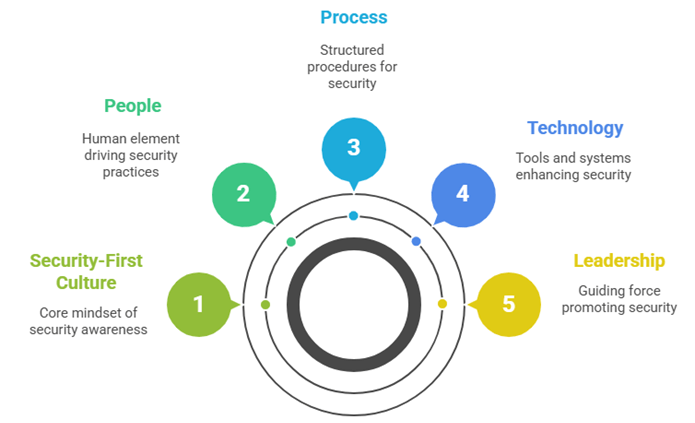
Fig 3.3: Security-First Culture
6️⃣ Measuring What Truly Matters
Compliance metrics show you progress on paper; security metrics show you progress against threats.

Real-World Proof: When Compliance Meets Maturity
Conclusion – From Audit-Ready to Attack-Ready
Compliance builds structure and confidence, it ensures accountability, governance, and trust.
But true cybersecurity maturity goes beyond certificates and checklists. It lies in risk awareness, continuous assurance, and the ability to adapt faster than adversaries evolve.
The journey from compliance to security is not a leap; it’s a transformation.
- Compliance lays the foundation.
- Operational execution bridges the gaps.
- Resilient security sustains protection through continuous validation and improvement.
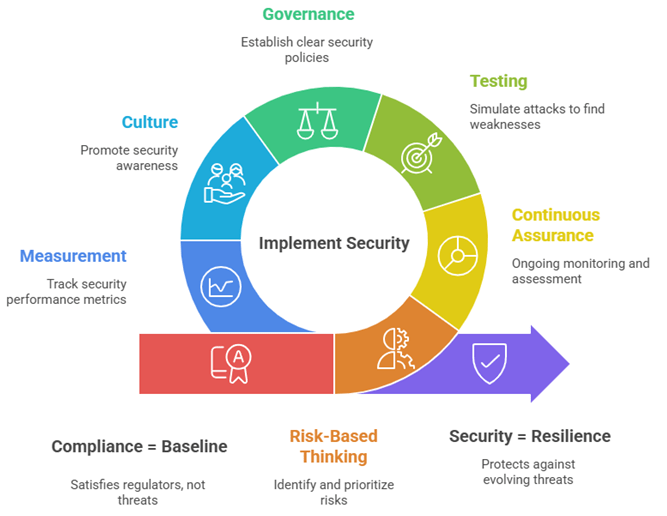
Fig 3.4: Building Resilience Through Security
A framed certificate may reassure auditors, but it won’t stop an exploit, a ransomware attack, or a misconfiguration.
Only a culture of proactive defense, live risk management, and adaptive controls can withstand today’s dynamic threat landscape.
Compliance keeps you audit-ready. Security keeps you attack-ready. Resilience keeps you future ready.
